Disclaimer: I am not associated in any way with the manufacturers and/or resellers of the products mentioned here. A lot of technical information has been (overly) simplified to facilitate understanding however I try to keep them as accurate as possible. The Gevey device in concern has just began shipping earlier this week, I have had very limited time with it so consider all information as preliminary and expect frequent updates/corrections. Your feedback and inputs are most appreciated, tweet @DillADH
For much of the last two years time, even the manufacturer of these SIM hack products acknowledge that their product is no longer needed; so it was quite a surprise when Gevey announced that they have something that will unlock the iPhone 4. Contrary to conspiracy theories, they withheld onto the product because:
- Initial production cost is high, they risk losing a lot of their investment should the dev team come up with a software unlock that does the same job if not better, before they were able to recover their cost.
- The exploit they used is not without serious problems, hence they were reluctant to produce it until there seems to be be no alternatives coming for a while.
- The exploit they used is very simple, provided you have the tools and skill, details to follow...
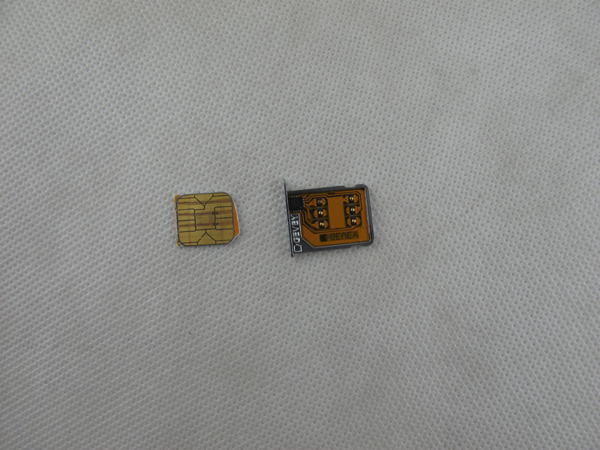
I have made a mistake earlier by calling it TurboSIM and it is not. @MuscleNerd reminded me of the correct term "
SIM interposer", since it sits electrically between the SIM card and baseband hardware to perform a classic
Man-in-the-middle Attack.
How did It Work?
SIM card holds many different types of information, but the part most involved with carrier lock is the IMSI number, which is a unique code that corresponds to your account in the mobile carrier's database.
A sample IMSI might look like this
310 150 987654321
The first two segments are known as Mobile Country Code (MCC) and Mobile Network Code (MNC) respectively, and in the example above the IMSI indicate the SIM is from USA (310) AT&T (150).
When the iPhone baseband is loaded into memory, it checks the MCC and MNC against its own network lock state stored in the seczone. If the combination is allowed, the cell radio is activated and vice versa.
The earliest iPhone baseband revisions only check IMSI twice following a restart, therefore it is very easy to spoof information in order to bypass the check. Nevertheless, the baseband was soon updated to validate SIM more aggressively and the method no longer works.
The Long Con
To guard against eavesdropping that plagued pre-GSM cellular networks, the initial connection to a network does not only involve IMSI, but a 4-byte TMSI to identify each handset before IMSI is sent. The base station recognises the IMSI as one of their users and replies with a
nonce (RAND) to the handset, where is signed with a 128bit key (Ki, stored encrypted on the SIM) and sent back. The network checks the string against their own result using the same RAND and Ki and allows the device to register if the two value matches.
You see, the IMSI is only sent once and never directly involved with authentication; as long as your key is valid, you will be able to get service. This is exactly what the various SIM hacks where a fake IMSI is sent along with the correct key.
The IMSI is redirected to another network and lost, In our case, the IMSI is invalid but some network proceed to the next step anyway - I will explain this in detail later.
Demise
The result of SIM hacks has always been erratic since the outcome depends on the implementation of the hack as well as the policies of the network; and people were inundated with a long list of issues and makeshift solutions. e.g. Cellular data may and may not work depending on the chemistry; a common remedy is to periodically put the hacked SIM into an unlocked "nanny" phone to "keep the TMSI fresh".
The use of SIM hacks fell sharply after iOS 2.2.1 update where the new baseband were made aware of the method and reject
dodgy exploitable IMSIs, even the better designed interposers suffered frequent failures. It is about the same time software unlocks were developed and it pushed SIM hacks further into disuse. However the technology has been kept alive since a number of GSM handsets, mainly those coming from Japan, remains vulnerable.
Partial Revival
Apparently somebody figured out that while the i4 baseband has been patched to prevent test IMSI from working, it is still possible to force activate the baseband using the emergency dialer.
After that, it is relatively the same trick all over again. Let's see what it does at each step.
You will need to use the SIM tray supplied and file your MicroSIM slightly to accommodate the EEPROM chip.
Installing the SIM + gevey.
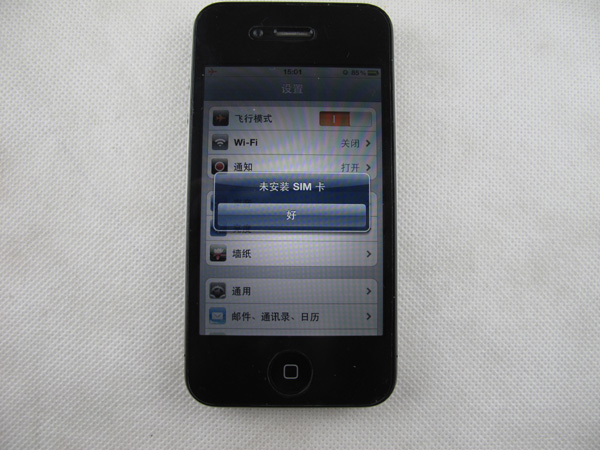
The phone will search for signal, comes up with no service and finally settling on this "one bar" icon.
At this stage the sim interposer is passing the parameters from the SIM as is. Earlier hacks required the fake IMSI to be programmed manually however this device is obviously capable of rapidly cycling a list of IMSI until an accepted MCC/MNC combination is found. pre-programmed with an exploitable IMSI. It may also spoof ICCID since the iOS is known to occasionally check that.
Dial 112 and hang up after the call is connected. The emergency call overrides the network lock and activates the cell radio. The network issues a TMSI for your real IMSI.
Toggle flight mode On/Off. Once the interposer senses flight mode, it transiently blocks electrical connection between the phone and the SIM (hence it will show "No SIM card installed") before sending spoofed IMSI. The BB allows the SIM and attempts to connect to network. What exactly happens is not too clear but apparently the interposer ROM block electrical connection to prevent the BB from detecting the fake IMSI.
The signal bars appear, we are safe:-) The network is able to register you again because the TMSI you obtained earlier is still valid, and the IMSI is not checked again. That is after the network ignored the fake IMSI (which the phone has no knowledge of) but allowed the SIM onboard because it is able to validate that.
Why 112?
112 had a long history as an emergency number for
practical reasons; back then when the GSM standard was being drafted in Europe, 112 was chosen to be the universal emergency number to call that can be called from any GSM phone, free of charge, with or without a SIM card on any compliant network.
However long before GSM service was established, 112 has been used to report landline faults in China; the coincidence made it unsuitable as a true emergency number. The network still connects 112 as an unbilled emergency call, only to play an automated message in both Chinese and English informing callers of the correct emergency numbers to dial; the call is never redirected.
What does it mean to unlockers?
- It works if A.your network handles 112 calls properly according to the GSM standard; B.they are
tolerant to TSMI spoofing lax on TMSI management and does not actively validate your IMSI again for incoming calls.
- Unlike its ancestors, the i4 SIM interposer is not a drop-in-and-forget device. The exact precedure must be followed everytime the device restart, lose reception for an extended period of time or move to another PLMN. In all situations the TMSI expires and has to be obtained again.
Theoretically it is possible for a daemon to automate the process similar to ZeroG, but that only makes thing more convoluted. Theoretically it is possible to reproduce the same behavior by physically switching your SIM card while flight mode is on.
- It is, without question, unethical or downright illegal to use the technique anywhere 112 is a legitmate emergency number. Use the exploit at your own risk/responsibility and tough luck if you get into trouble with the law.
- All firmware/baseband combinations for the i4 up to iOS
4.3 4.3.1 are vulnerable, however the exploit may be patched in any future software updates or via the carrier.
- SIM interposer should not harm your phone hardware, however your network could request IMEI and identify your device during the emergency call, leading to your handset getting banned. Your identity cannot be faked and it is possible that they will shut down your account. There is a reason why SIM cards remain legally the property of the service provider: you are not supposed to tamper with them without breaching contract.
- Notwithstanding all the problems, SIM interposer does not cause any battery drain since it is only active transiently (at least for the gevey, some clones may use less reliable components and cause issues), nor would it cause signal loss as long as you stay in the same cell - TMSI may be reused in the neighboring one since it is only 4 bytes.
Conclusion:
An overpriced (
US$50 US$70, although clones are just starting to appear), unreliable and legally questionable mod; works for some but your mileage may vary; get it if you are desperate or wait for the
40-bit 56-bit NCK hack or the eventual SW unlock by the iPhone dev team.